陇原战"疫"2021网络安全大赛_RE_WP
陇原战”疫”2021网络安全大赛_RE_WP
EasyRe
方法一
IDA打开分析
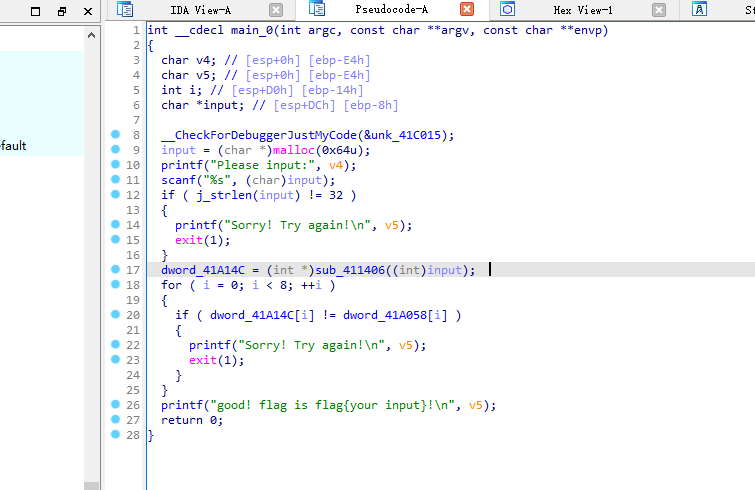
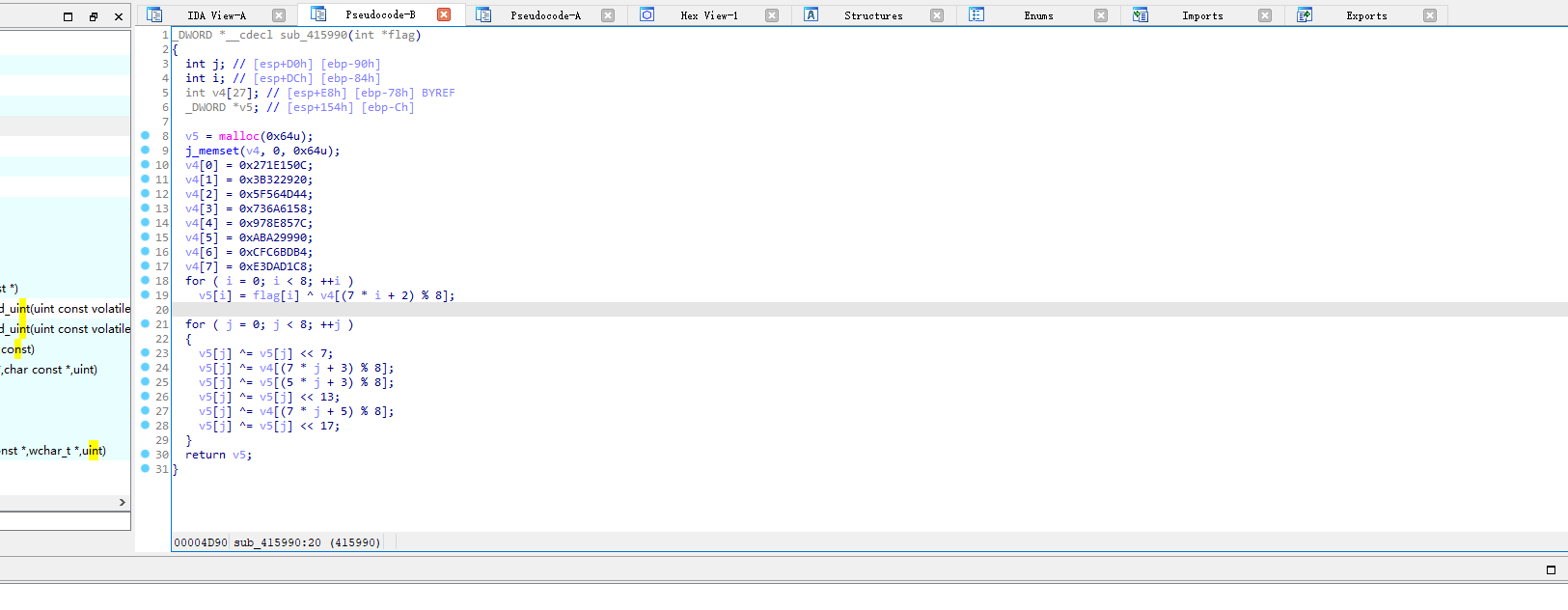
发现sub_4111406这个函数是对输入的flag进行加密,然后将加密后的数据存放到0X41A14C中
来到sub_4111406函数,并不能F5, 直接动态调试一直跟
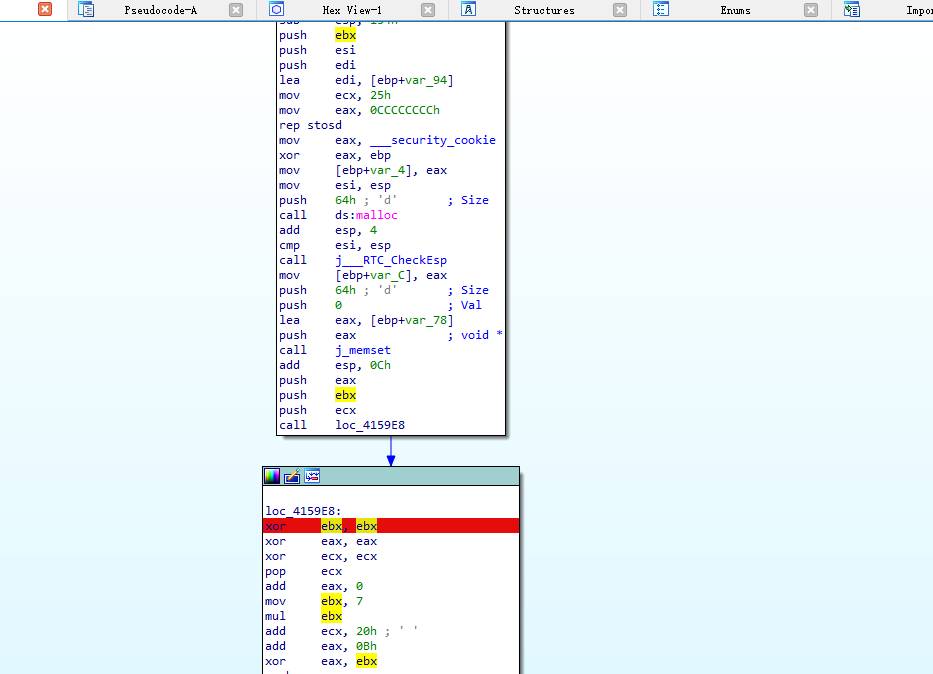 、
、
发现程序在不断的生成一些数据,长度是32
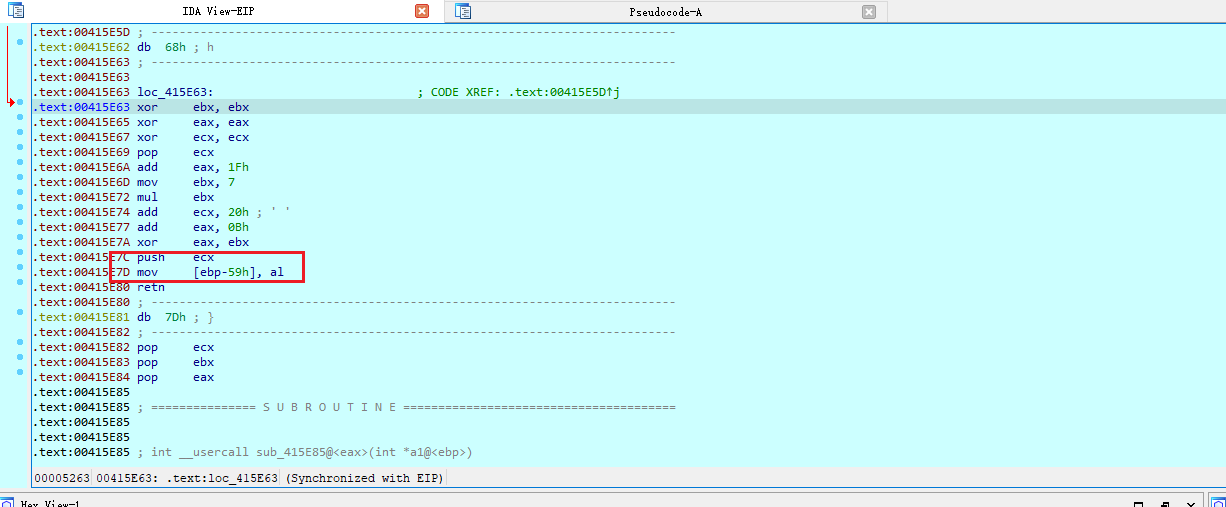
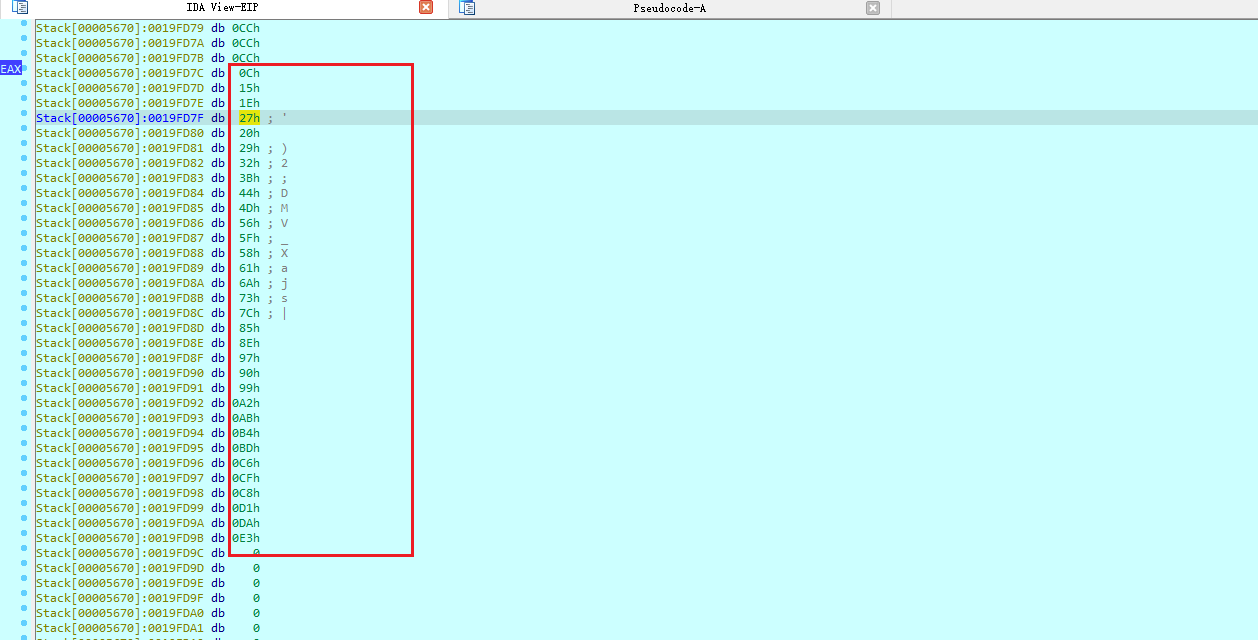
多次调试,不同输入,这里获取的数据是一样的
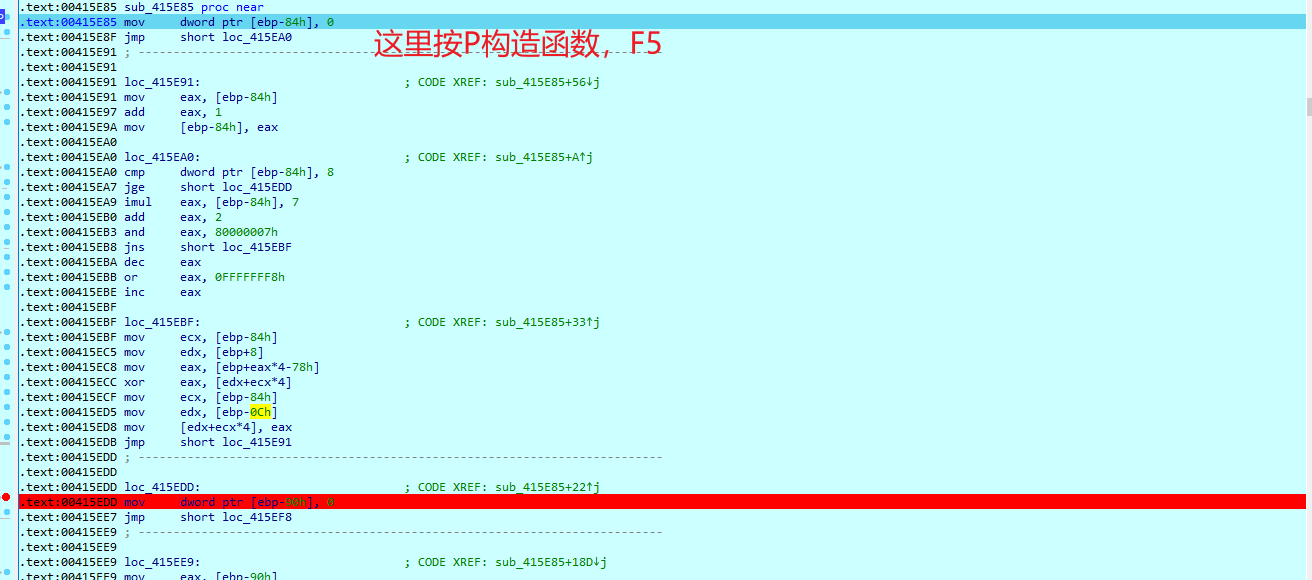
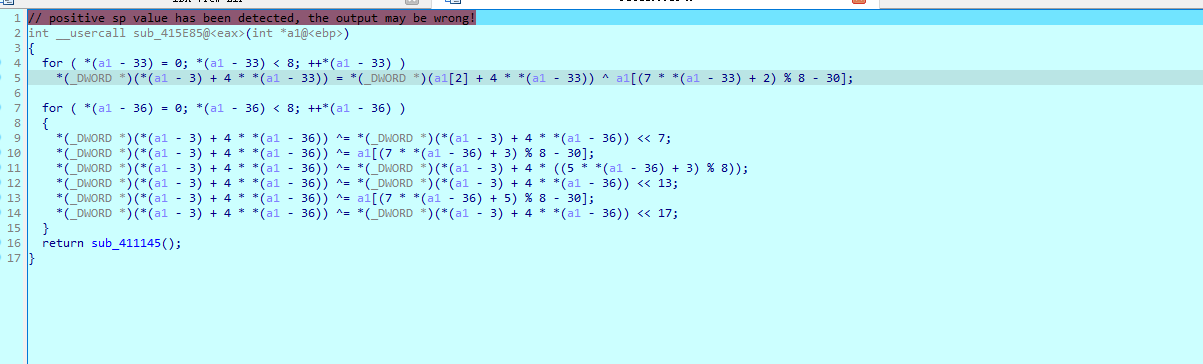
分析,还原算法
1 |
|
在末尾下断点调试
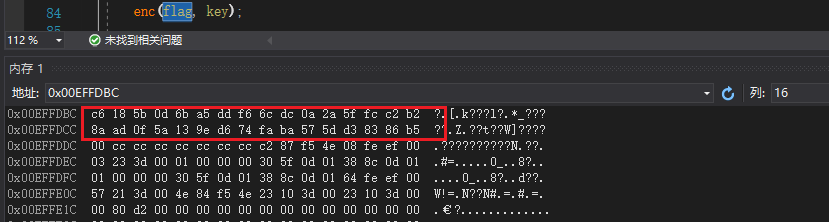
IDA调试运行下断点观察加密后的数据
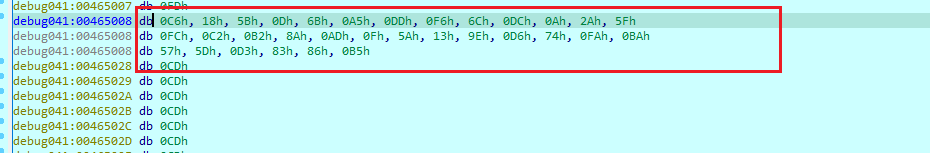
发现是一样的,还原加密算法成功,现在开始写解密脚本
1 |
|
得到 fc5e038d38a57032085441e7fe7010b0,加上 flag{} 得到 flag{fc5e038d38a57032085441e7fe7010b0}
方法二
去花指令
1 | from ida_bytes import get_bytes, patch_bytes |
Z3模块解决
1 | from z3 import * |
EasyRe_Revenge
此题与EasyRe_Revenge一样,只是把密文换了,替换上图中的enc_flag即可
1 | char enc_flag[33] = { 66, 176, 232, 238, 108, 238, 208, 87, 50, 75, 245, 243, 214, 183, 240, 211, 137, 195, 97, 10, 64, 186, 199, 56, 44, 158, 61, 12, 132, 146, 74, 214,0 }; |
后来发现,原来EasyRe那道题目,flag直接存在字符串中了,所以把密文换了,才有了这个EasyRe_Revenge
findme
IDA打开分析
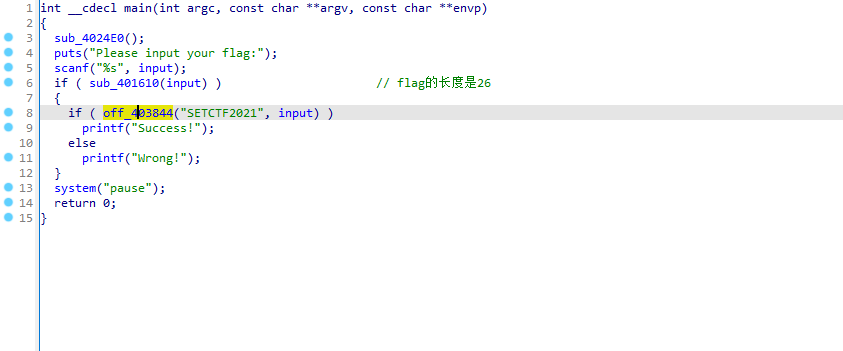
来到 403844 这个位置
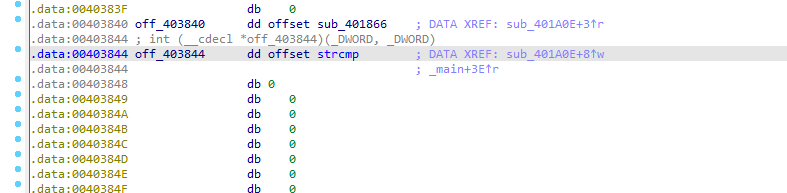
很显然这个位置不可能是strcmp,观察发现404840那个地址处还存了个函数的地址 sub_401866,估计程序有地方把403844这个地方的地址给替换掉了
来到401866位置
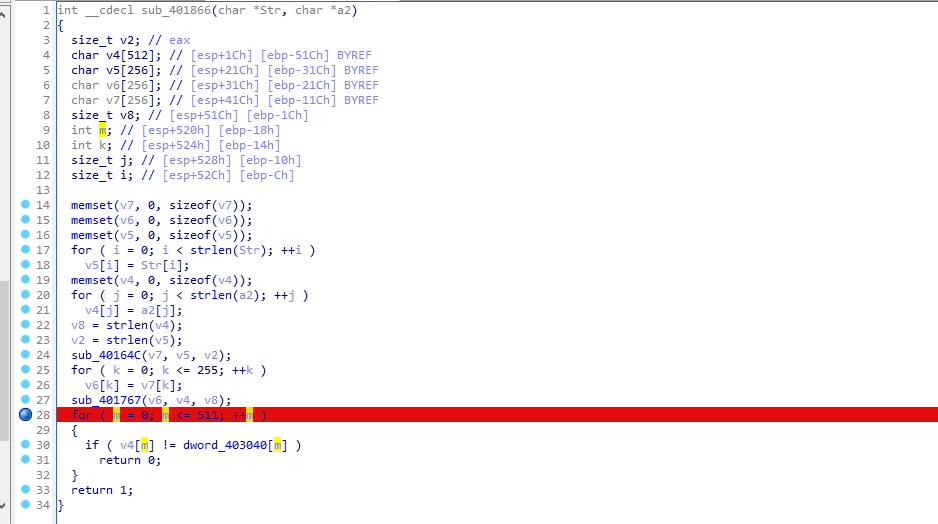
分析401767函数,发现是明显的RC4加密
随便输入一个假的flag,12345678901234567890123456, 然后断下,看加密后的数据
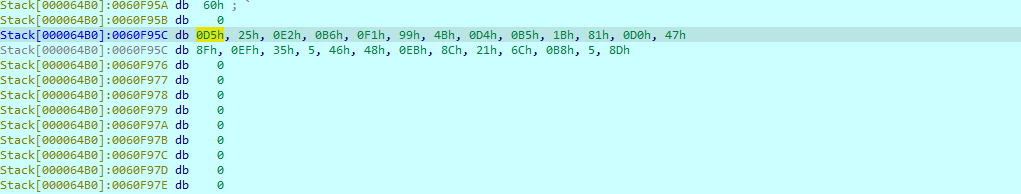
写脚本得到密钥流
1 | fake_flag = "12345678901234567890123456" |
然后提取出dword_403040解密即可
1 | enc = [0xFFFFFFB7, 0x52, 0x0FFFFFF85, 0x0FFFFFFC1, 0x0FFFFFF90, 0x0FFFFFFE9, 0x7, 0xFFFFFFB8, 0x0FFFFFFE4, 0x1A, 0x0FFFFFFC3, 0x0FFFFFFBD, 0x1D, 0x0FFFFFF8E, 0x0FFFFFF85, 0x46, 0x0, 0x21, 0x44, 0x0FFFFFFAF, 0x0FFFFFFEF, 0x70, 0x32, 0x0FFFFFFB5, 0x11, 0x0FFFFFFC6] |
power
拿到题目,附件是ARM汇编源文件
直接用arm-none-eabi-as.exe power编译下生成a.out
IDA打开
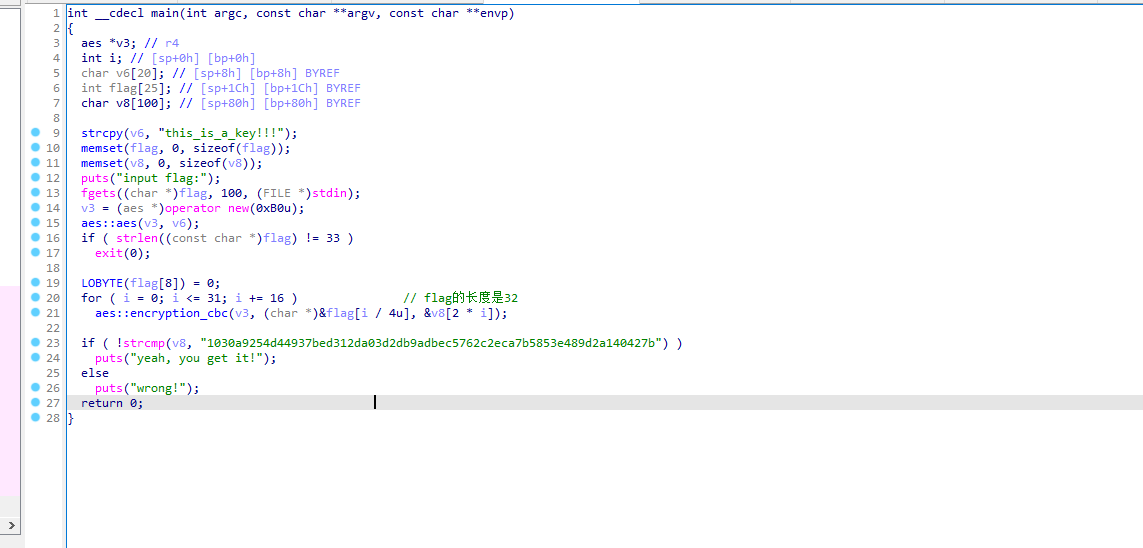
发现是AES加密,这里写的是CBC模式,但其实是ECB模式,写脚本解密即可
1 | from Crypto.Cipher import AES |
Eat_something
核心代码在Eat_something.wasm中
找到工具将wasm转为.o文件 https://www.52pojie.cn/thread-1438499-1-1.html
用IDA打开,找到w2c_checkright函数,这是验证flag的地方
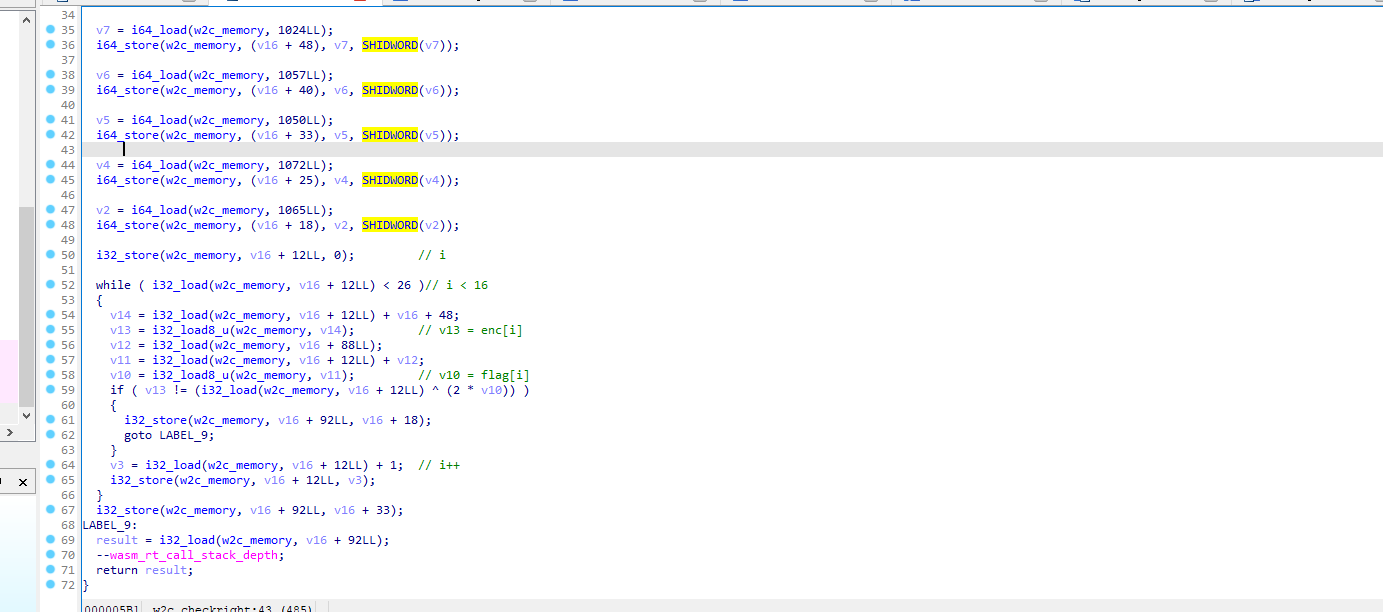
核心算法就是这一句 v13 != (i32_load(w2c_memory, v16 + 12LL) ^ (2 * v10))
翻译下就是enc[i] != i ^ (flag[i] * 2)
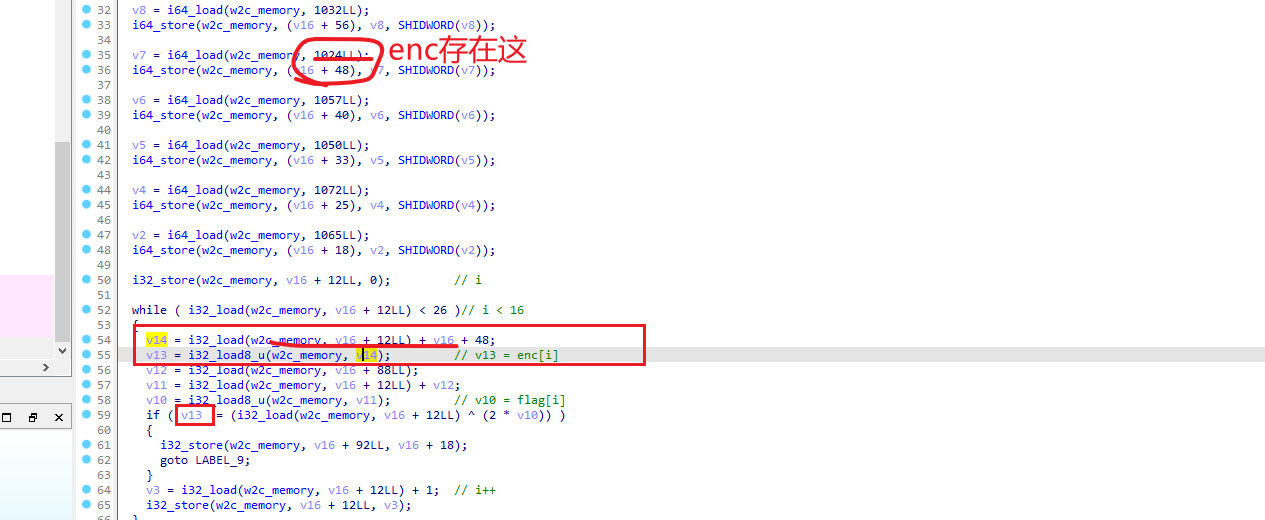
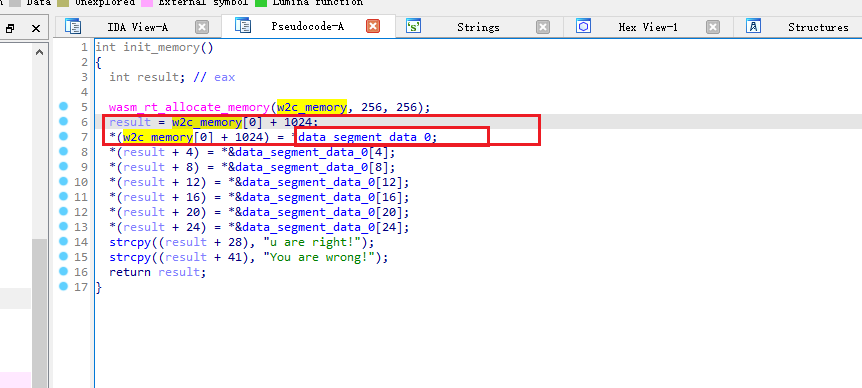
将enc提取出来,写脚本即可
1 | enc = [0x86, 0x8B, 0xAA, 0x85, 0xAC, 0x89, 0xF0, 0xAF, 0xD8, 0x69, |
最后将CETCTF 改为 SETCTF即为flag

