VNCTF2022_RE_复盘
VNCTF2022_RE_复盘
1.BabyMaze
题目给出一个 BabyMaze.pyc 文件,尝试用uncompyle6反编译,但是失败 ,于是用脚本反汇编
1 | # 安装环境 |
1 | 1 0 JUMP_ABSOLUTE 4 |
可以发现开头是3个指令的跳转,是这个地方干扰了uncompyle6,于是打开opcode.h,找对应的机器码

是113(0X71)
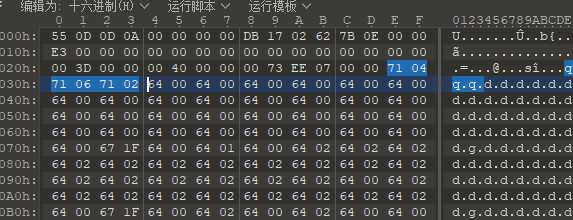
将其删除,并且将 7EE 改为 7E8,然后重新反编译
1 | # uncompyle6 version 3.7.4 |
发现是31 * 31的迷宫
稍作整理,DFS解密即可, 解密脚本如下
1 | # 题目:给定大小为n*m的矩阵,求S到G的最短路径并输出 |
关于python字节码的反汇编,可以看这个文章学习 https://song-10.gitee.io/2020/04/20/Reverse-2020-04-20-python-byte/
2.cm1
是个APK文件,拖入JEB进行分析
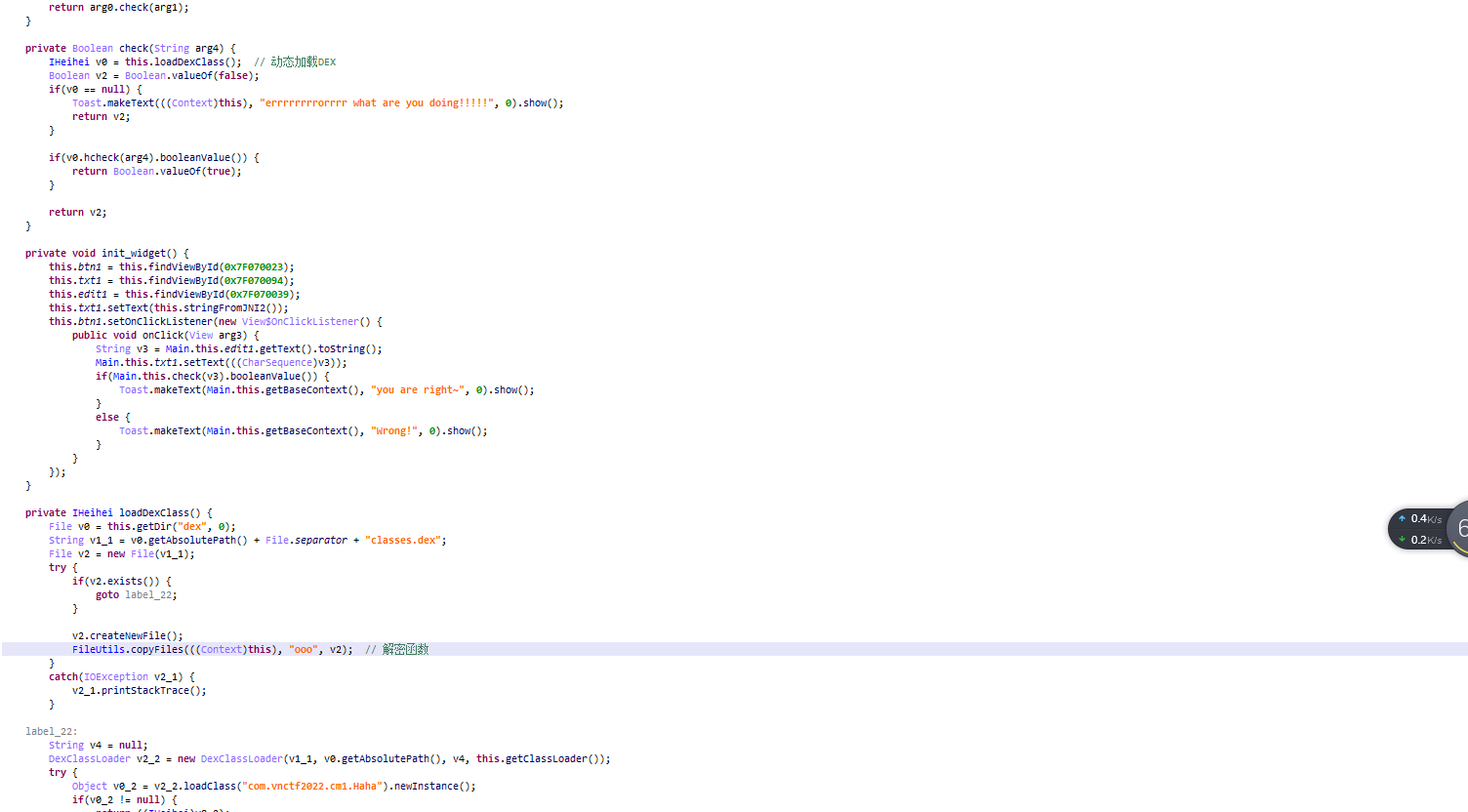
发现关键check函数放在了解密后的ooo文件中,进入copyFiles函数观察如何解密的
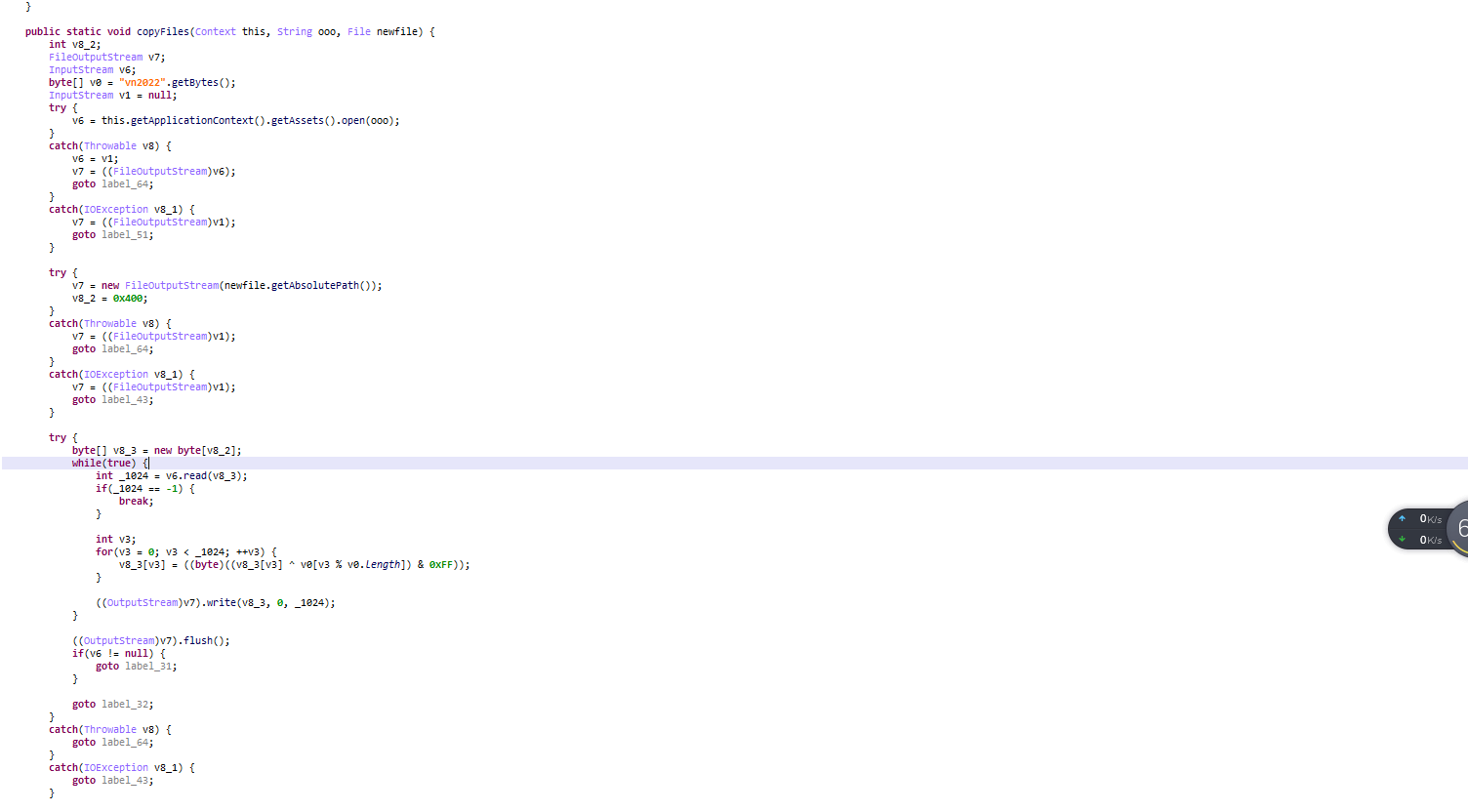
是以1024为1组,异或vn2022,写脚本解密
1 | with open("ooo", "rb") as f: |
然后用jadx打开opoo,找到hcheck

是xxtea加密,写脚本解密即可
1 | In [18]: a = b"H4pPY_VNCTF!!OvO" |
1 |
|
3.cm狗
拿到题目,发现是用go语言实现的VM,直接用IDA7.6打开
根据main.(_ptr_MzVm).init 和 main.(_ptr_MzVm).run 2个函数,找到VM的大体结构
1 | struct func |
添加结构体到IDA中,发现瞬间函数变的非常的清晰

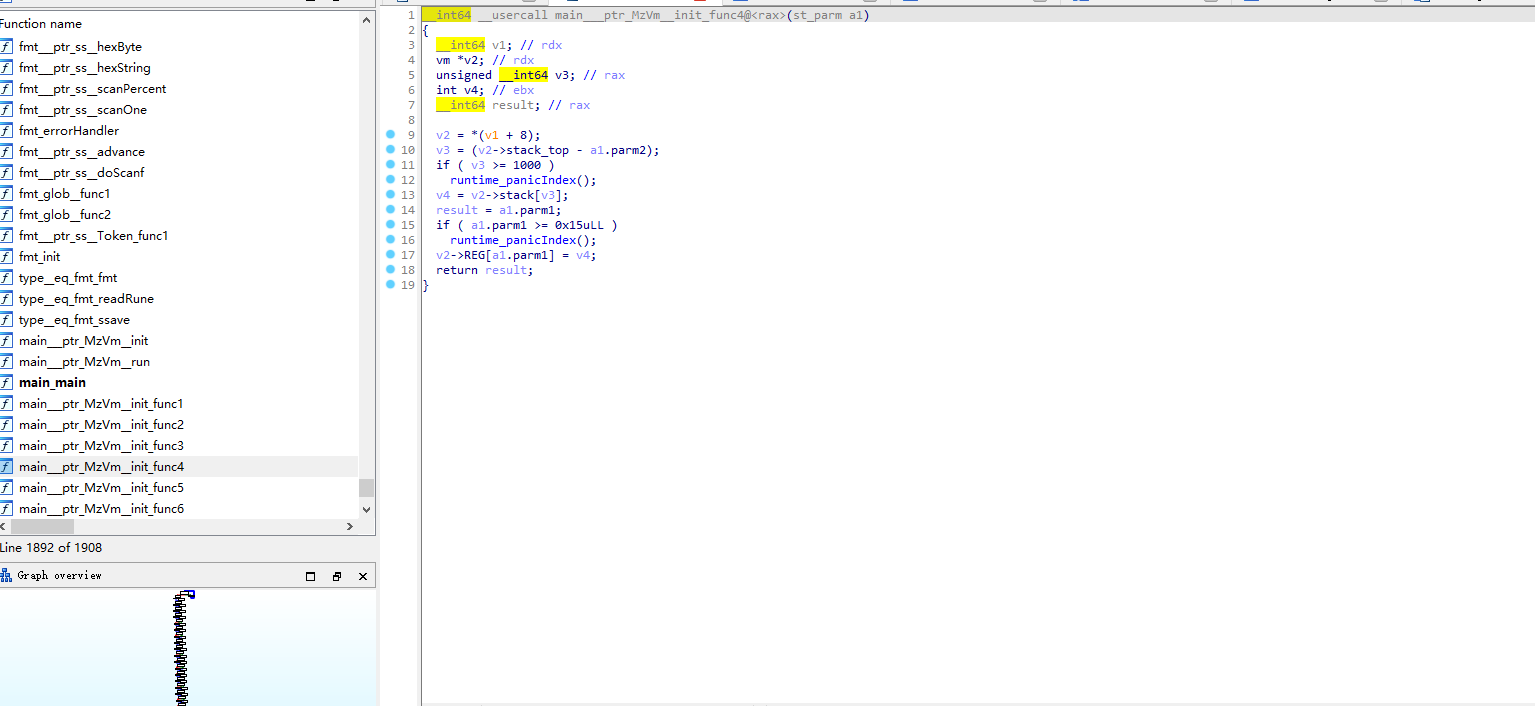
慢慢分析每个func的功能,然后把OPCODE提取出来,写脚本打印伪代码
1 | a = [0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000057, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000065, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000006C, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000063, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000006F, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000006D, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000065, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000020, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000074, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000006F, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000020, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000056, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000004E, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000043, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000054, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000046, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000032, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000030, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000032, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000032, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000021, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000000A, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000069, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000006E, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000070, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000075, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000074, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000020, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000066, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000006C, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000061, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x00000067, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000003A, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000000, 0x0000000A, 0x00000062, 0x00000000, 0x00000000, 0x00000001, 0x00000013, 0x00000049, 0x00000001, 0x00000003, 0x00000000, 0x00000001, 0x00000001, 0x0000002B, 0x00000001, 0x00000002, 0x00000001, 0x00000061, 0x00000000, 0x00000000, 0x00000005, 0x00000000, 0x00000000, 0x00000008, 0x00000001, 0x00000002, 0x0000000E, 0x00000001, 0x00000003, 0x00000001, 0x00000000, 0x00000000, 0x00000005, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000006, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000006, 0x00000000, 0x00000002, 0x00000000, 0x00000006, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000006, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000006, 0x00000000, 0x00000002, 0x00000000, 0x00000006, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000006, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000006, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000007, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000007, 0x00000000, 0x00000002, 0x00000000, 0x00000007, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000007, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000007, 0x00000000, 0x00000002, 0x00000000, 0x00000007, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000007, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000007, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000008, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000008, 0x00000000, 0x00000002, 0x00000000, 0x00000008, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000008, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000008, 0x00000000, 0x00000002, 0x00000000, 0x00000008, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000008, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000008, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000009, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000009, 0x00000000, 0x00000002, 0x00000000, 0x00000009, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000009, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000009, 0x00000000, 0x00000002, 0x00000000, 0x00000009, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x00000009, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x00000009, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000A, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000A, 0x00000000, 0x00000002, 0x00000000, 0x0000000A, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000A, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000A, 0x00000000, 0x00000002, 0x00000000, 0x0000000A, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000A, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000A, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000B, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000B, 0x00000000, 0x00000002, 0x00000000, 0x0000000B, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000B, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000B, 0x00000000, 0x00000002, 0x00000000, 0x0000000B, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000B, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000B, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000C, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000C, 0x00000000, 0x00000002, 0x00000000, 0x0000000C, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000C, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000C, 0x00000000, 0x00000002, 0x00000000, 0x0000000C, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000C, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000C, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000001, 0x00000005, 0x00000100, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000D, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000D, 0x00000000, 0x00000002, 0x00000000, 0x0000000D, 0x0000000A, 0x00000000, 0x00000005, 0x00000002, 0x0000000D, 0x00000000, 0x00000006, 0x00000000, 0x00000000, 0x00000007, 0x0000000D, 0x00000000, 0x00000002, 0x00000000, |
1 | VM->REG[0] = 87 |
一点点分析,发现是tea加密,提取出密文和key,解密即可
1 |
|
4.时空飞行
IDA打开,发现流程非常的清晰,就是时间的问题。。。
先判断输入的日期
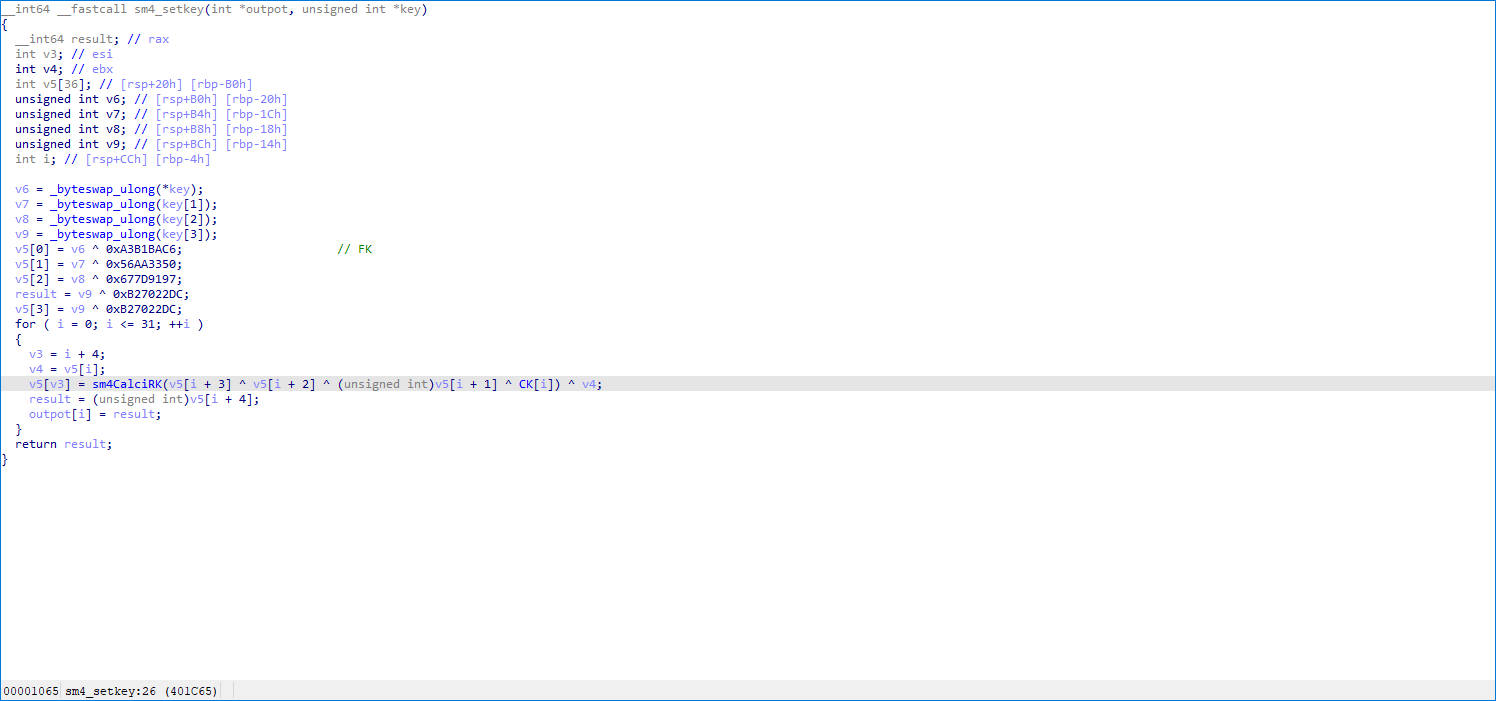
写脚本直接逆即可
1 | from z3 import * |
然后再往下,用Z3解
1 | from z3 import * |
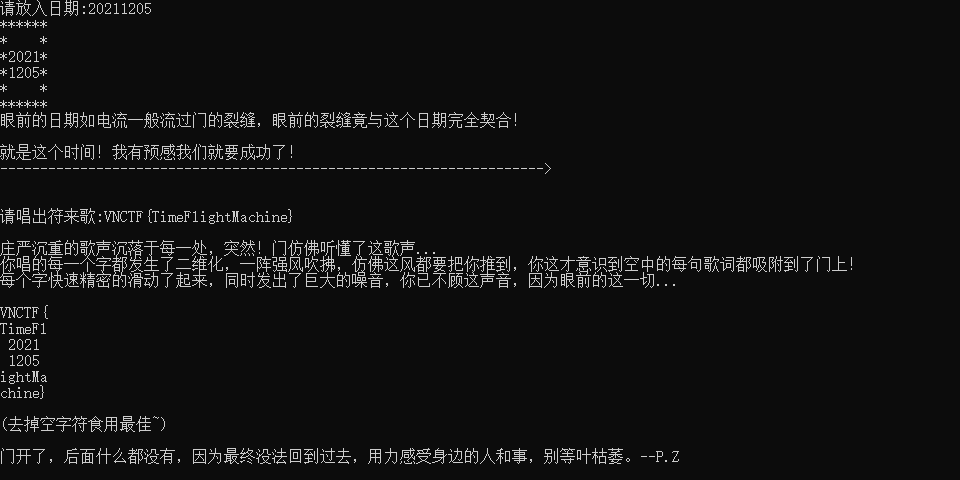
去掉空字符为flag: VNCTF{TimeFl20211205ightMachine}
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 zsky's Blog!
评论

